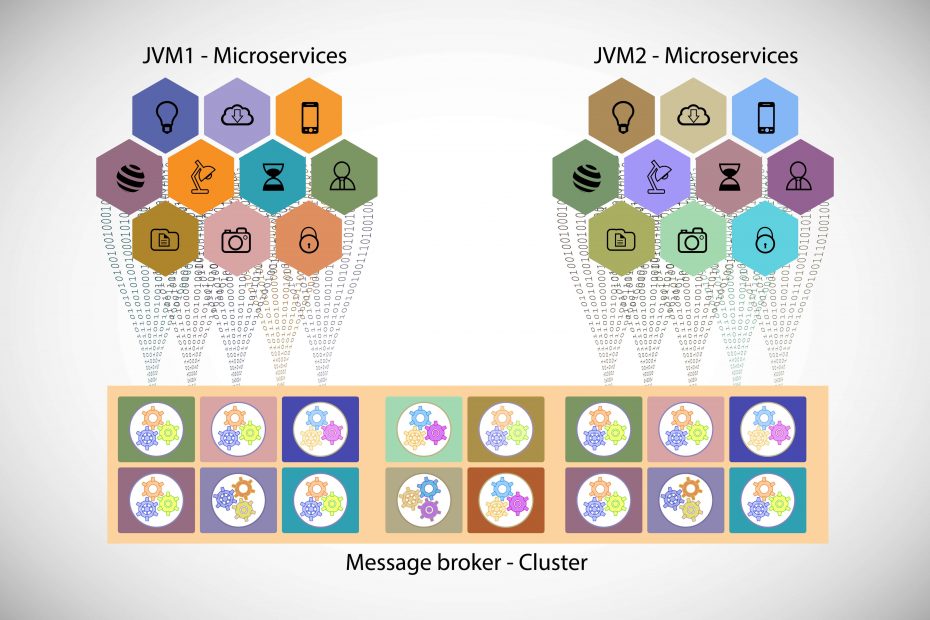
Security Modeling for Reliability and Resilience
What are Security Models Information systems use security models, which are a list of operations for evaluating and authenticating security policies. This helps to map policy goals to information systems through the specification of explicit data structures and techniques needed for implementing the said security policy. A security model can be represented in mathematical form as well as analytical ideas.… Continue readingSecurity Modeling for Reliability and Resilience