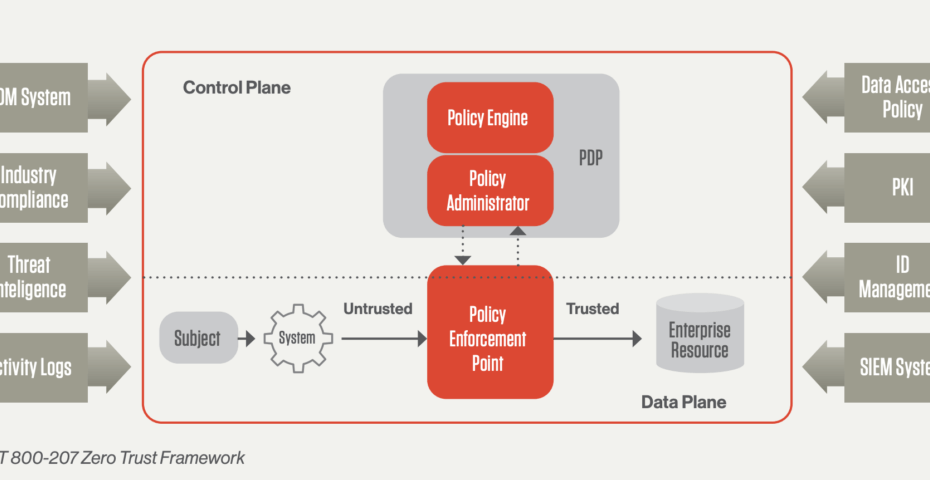
Scrum | A framework to achieve (when it isn’t marred by misleading metrics)
If you’re familiar with the Scrum framework, you’ll know that it’s an agile approach to project management that helps software teams worldwide tackle increasingly complex projects. Despite the common perception that it’s inherently linked to software development, Scrum is actually a philosophy of work, a way of thinking about and breaking down tasks that focuses on adaptability and quick turnovers.… Continue readingScrum | A framework to achieve (when it isn’t marred by misleading metrics)