Mobile and IoT Security Strategies in the Cloud
Internet of Things (IoT) has become incredibly popular in recent years. As it expands and incorporates more “smart” products, it creates connections between homes, factories, and even cities. In fact, according to McKinsey’s research data, the IoT market is all set to experience annual growth and valuation, reaching up to $11.5 trillion by 2025.
However, as amazing as this growth, the smart connection reliability of technology has IoT become, it has its due risks and challenges involved. This means that although you may easily buy the luxury of a smart home with connected vacuum Robots, doorbell cameras, smart temperature controls, and locks – there are little to no security risks taken into account
Believe it or not, many smart product developers don’t consider prioritizing security challenges presented by the product. They carry on with the product in the market until a security breach or data leak compromises their brand image and sales. The latest upgrades are made to the product and made available in Volume 2 of the product launch.
Thus, this doesn’t come as a shocker that seemingly one of the most important concerns, such as security, is right now one of the biggest impending disasters of IoT device manufacturers. As per Garner’s survey findings, IoT risk assessment has recently taken a turn in two steps: vulnerability scanning and IoT network segmentation.
Service-Disabled Veteran-Owned Small Business (SDVOSB)
Small Disadvantaged Business (SDB)
Small Disadvantaged Business leads to enhanced innovation and creativity, as these businesses often offer unique perspectives and solutions shaped by their diverse backgrounds. Moreover, partnering with Small Disadvantaged Business can provide access to specialized skills and capabilities that might otherwise be overlooked, contributing to improved competitiveness and efficiency.

Transforming for Innovation, Sustainability and Security
Transforming for Innovation and Sustainability securing future competitive advantage
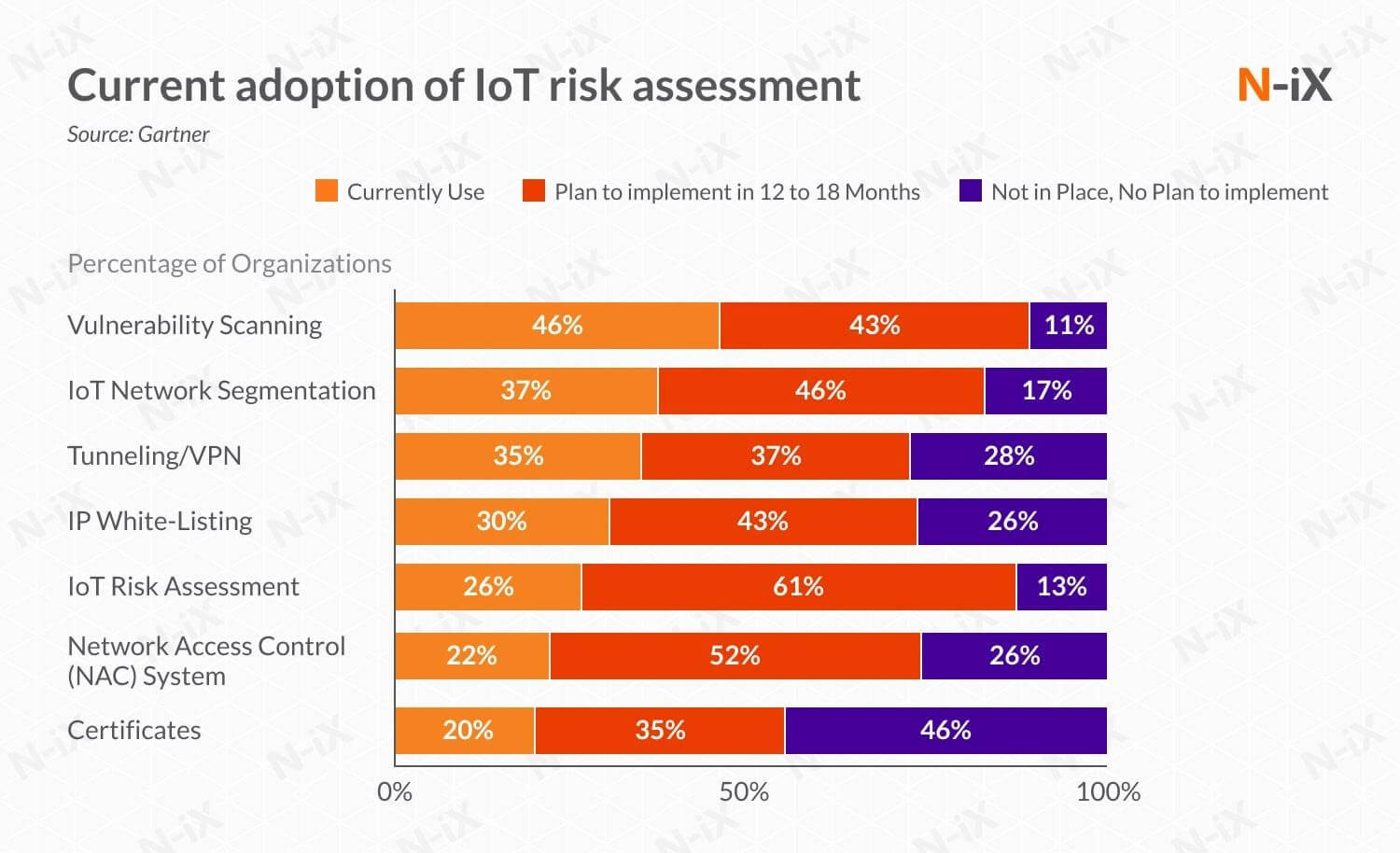
Although this shows that as of 2021, IoT and public clouds would have almost 60% fewer security issues than a while back in traditional data domains – there are still some challenges that need to be addressed and consequently mitigated. So let’s look at some primary IoT cloud security issues and strategies to mitigate them.
Common IoT Cloud Security Risks
Following are some of the most common IoT cloud security risks that need to be addressed and strategized for a solution.
Lack of Awareness in Users
First, the number one IoT cloud security problem is due to a lack of awareness in IoT and Cloud product users. From regular training of the employees to creating awareness channels for the end-user, each user needs to enhance security awareness in every way possible.
Outdated Device Software
The software of the majority of the IoT devices is often outdated, which in turn severely compromises the security of the device and the user. It makes the product vulnerable to hacking, creating substantial threatening security loops. Therefore, managing updates for IoT devices is an absolute must for every user to minimize the system’s vulnerabilities.
Device Authentication Issues
Many devices such as smartphones and smart TVs have authentication issues when connecting and coordinating data transfer with their devices. These authentication issues create vulnerable security loops for hackers. For instance, it becomes easy for a hacker to hack your camera or microphone and record audio and video illegally.
No Built-In Security Patches
Often, when an IoT device requires an update to be installed, it doesn’t have enough storage space to do so. The primary reason for such a thing is that IoT product manufacturers prioritize other factors over security. Hence, choosing hardware with a built-in security patch installation storage is always a good idea.
Top 5 Best Practice Strategies to Ensure IoT Cloud Security
Now that you know the looming dangers of IoT cloud security issues let’s look at some of the best practice strategies you can incorporate in your homes and businesses to mitigate them.
1. Automated Security Monitoring
It is an integral part of conducting thorough IoT cloud security strategies. If you do not watch your IoT devices and infrastructure, the chances are high that your system is way more susceptible to security and data breaches. Therefore, configuring network firewalls and monitoring central IoT systems is great.
2. Integrated Approach for IoT Cloud Security
For IoT device manufacturers, it is essential to focus on integrating security measures within the device along the production stages. The main reason this should happen is that integrated security measures and features to be introduced post-production can present extremely challenging given how most of the devices have already been sold.
3. Categorize On-Premises Data
Security might be very important for many cloud providers, but IoT cloud integration can easily mess things up. Therefore, categorizing certain information as what can be safely placed on the cloud and what should always remain as on-premises data on your hardware is crucial—for instance, personal data like healthcare information, financials, and identity documents.
4. Use DevSecOps for Your Advantage
DevSecOps is the new alpha in town regarding IoT cloud security. Therefore, it only makes sense to use the new and advanced technology to your advantage. It allows for security features to be integrated within IoT devices every step of the way. Moreover, introducing this earlier in the developmental stage greatly minimizes the security risk.
5. Partner With an Established Security Policy Holder
It is good news that more than 60% of businesses will be investing in IoT cloud security risk assessment within the next 18 months. This increases the need for adequate cloud security professionals. Consequently, many businesses partner with established security policyholders to achieve enhanced IoT cloud security.
Generative AI Software Integration
Boost your business efficiency with our custom Generative AI Business Software, tailored for HR, finance, sales, event management, and customer service. Leveraging advanced natural language processing and AI-driven data science, we specialize in customer segmentation, sales analysis, and lead scoring. Elevate your operations and gain a competitive advantage with our precision-driven AI solutions. Contact us to integrate AI seamlessly into your key systems and transform your business.
What clients say about Cloud Computing Technologies
★★★★★ 5/5
"CCT's diverse skills and expertise has reduced our technical debt by millions of dollars to which we have reinvested into future capabilities."

Mrs. Hanson
★★★★★ 5/5
"With CCT migrating our critical systems into the AWS, 80% our staff is now remote working."

Mrs. Miller
★★★★★ 5/5
"CCT showed us how to meeting regulatory compliance in AWS Landing Zone and greatly improved our cloud security controls."

Mrs. Wilson
★★★★★ 5/5
"CCT provided our agency with application rationalization services and successfuly applicaton migrations meeting all KPIs and SLAs."

Federal Agency
★★★★★ 5/5
"I highly recommend the data science team at CCT. They are technically proficient, great communicators, unbiased, and reduced our false positives by 68%."

Mr. Brown
★★★★★ 5/5
"The team at CCT is knowledgable and insightful in developing a cloud architecture leading to our mission success."

Mr. Robinson
Experience and Agile Expertise
you can trust
Years in business
20
Contracts Awarded
180
+
Conclusion for Mobile and IoT Security Strategies in the Cloud
It is only a matter of time before IoT product manufacturers realize that security poses a severe threat to the users and take actions to mitigate and manage them. Until then, as a responsible IoT cloud security enabler, you can take steps on your own to stay on the safe side.
At Cloud Computing Technologies, we take pride in guiding our customers through their IoT cloud security management. We offer secure, scalable, and fully on-demand cloud services through our enterprise-level cloud partners like Amazon AWS.
If you’d like to find out more information about Mobile and IoT Security Strategies in the Cloud offerings, or if you’d just like to discuss your own needs with someone in a bit more detail, please don’t delay – contact Cloud Computing Technologies today.
Further information about Mobile and IoT Security Strategies in the Cloud.